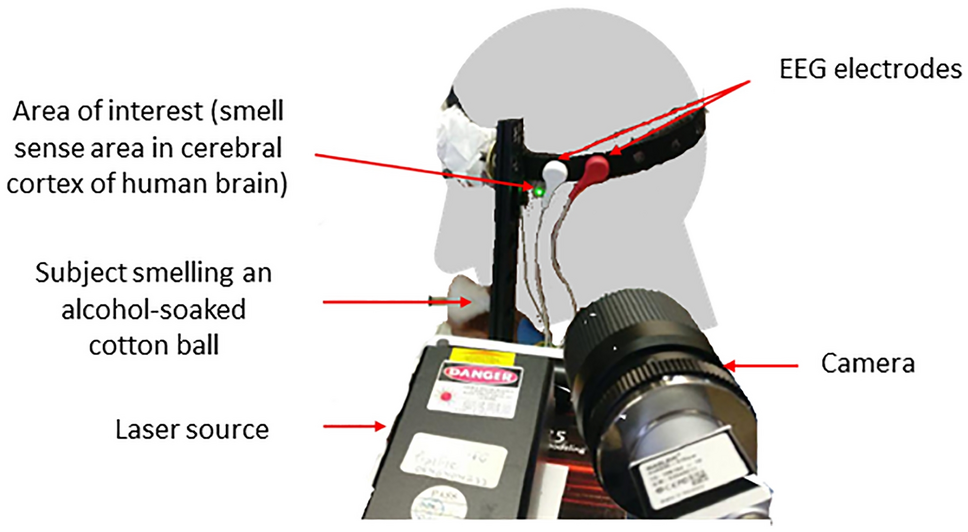
Infection control in the intensive care unit: expert consensus statements for SARS-CoV-2 using a Delphi method - The Lancet Infectious Diseases
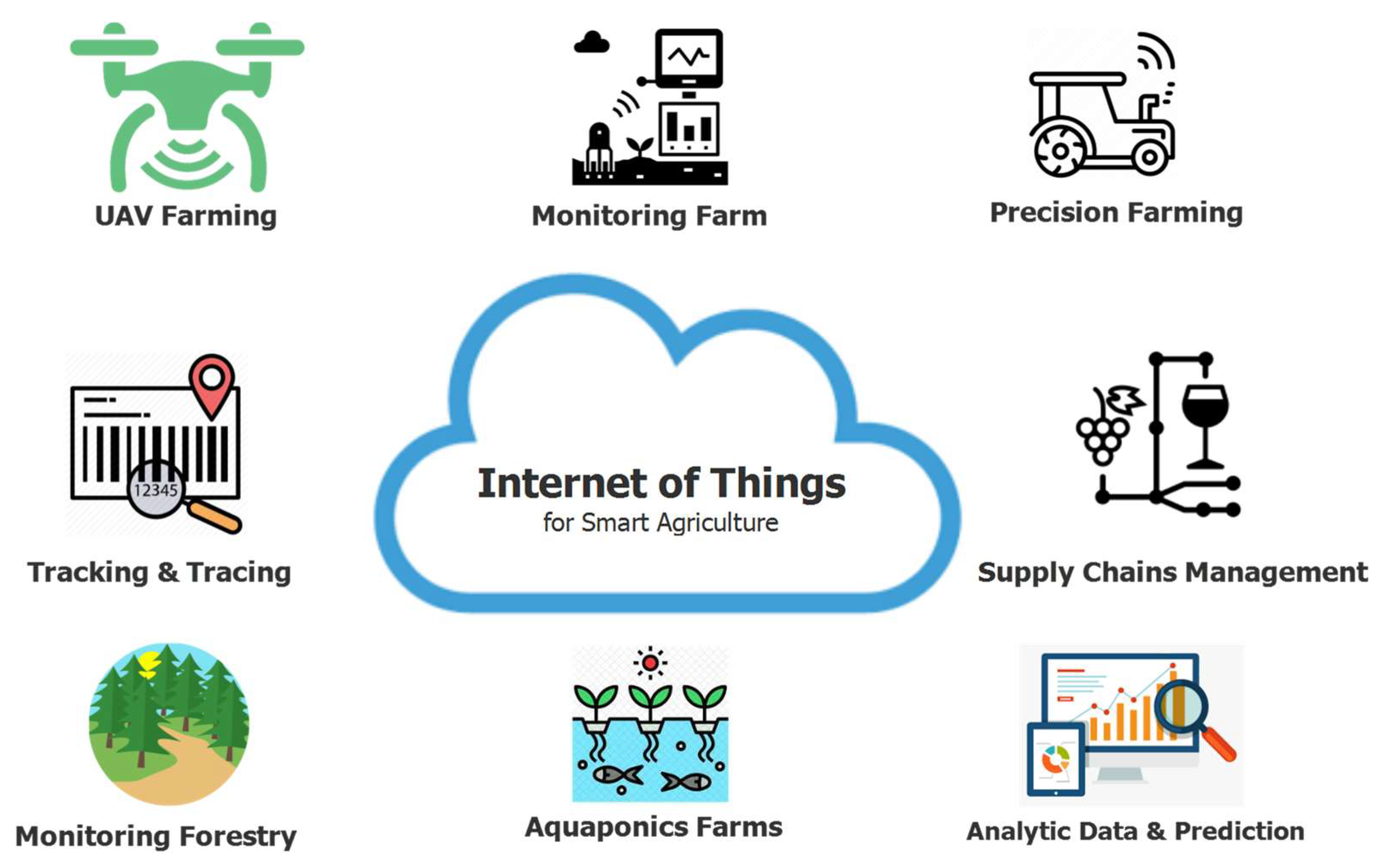
Applied Sciences | Free Full-Text | IoT-Enabled Smart Agriculture: Architecture, Applications, and Challenges
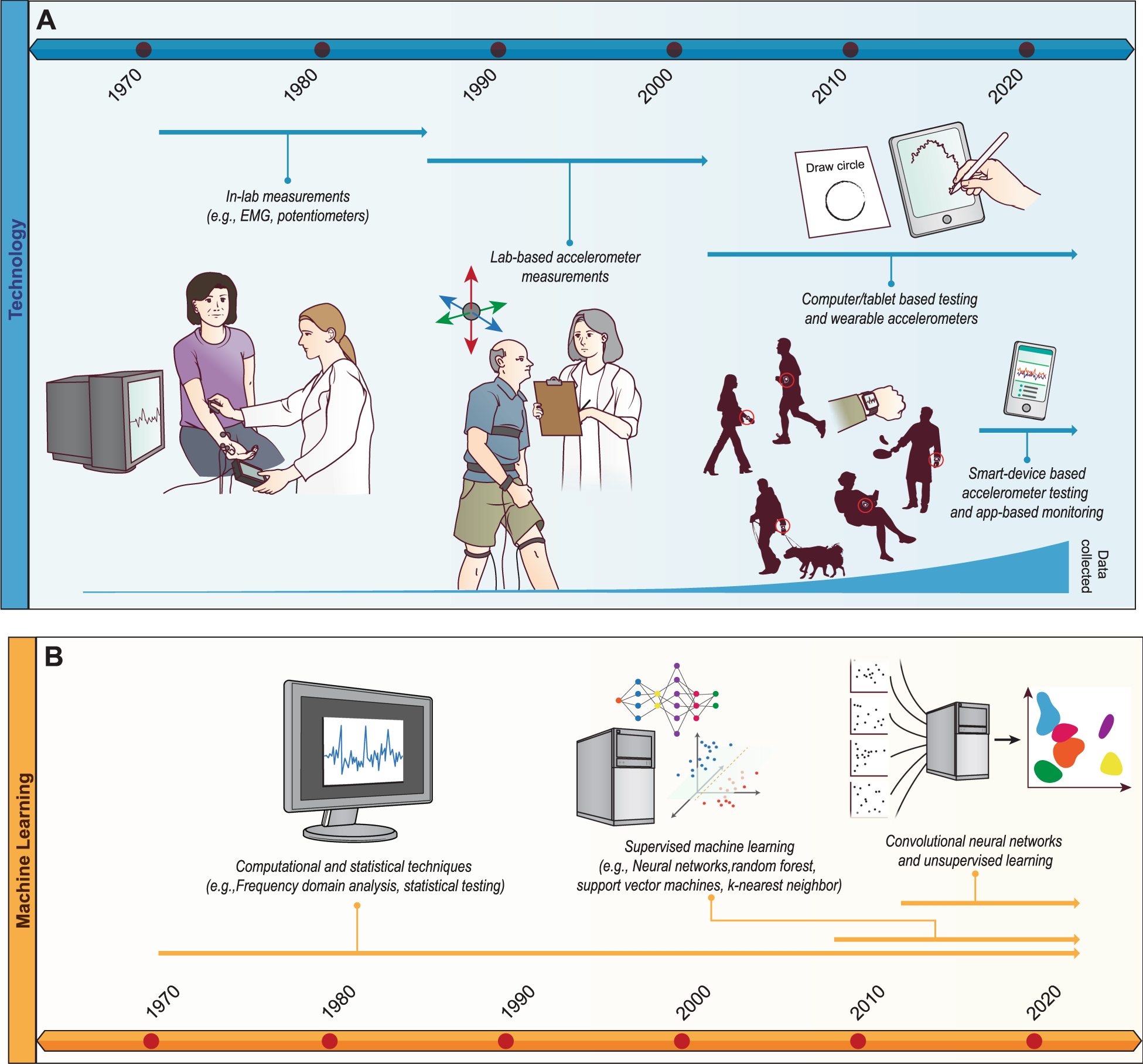
Co-evolution of machine learning and digital technologies to improve monitoring of Parkinson's disease motor symptoms | npj Digital Medicine

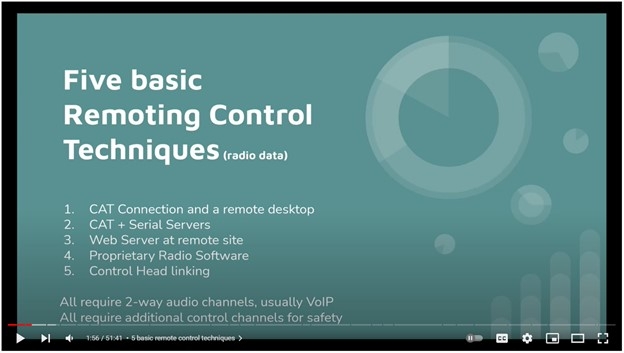
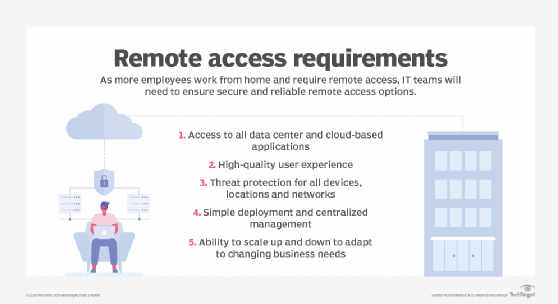
Boundless: Your How To Guide to Practical Remote Viewing - Phase One (A How To Series to Learn Controlled Remote Viewing Book 1) eBook : Lambert Williams, Lori: Amazon.co.uk: Kindle Store
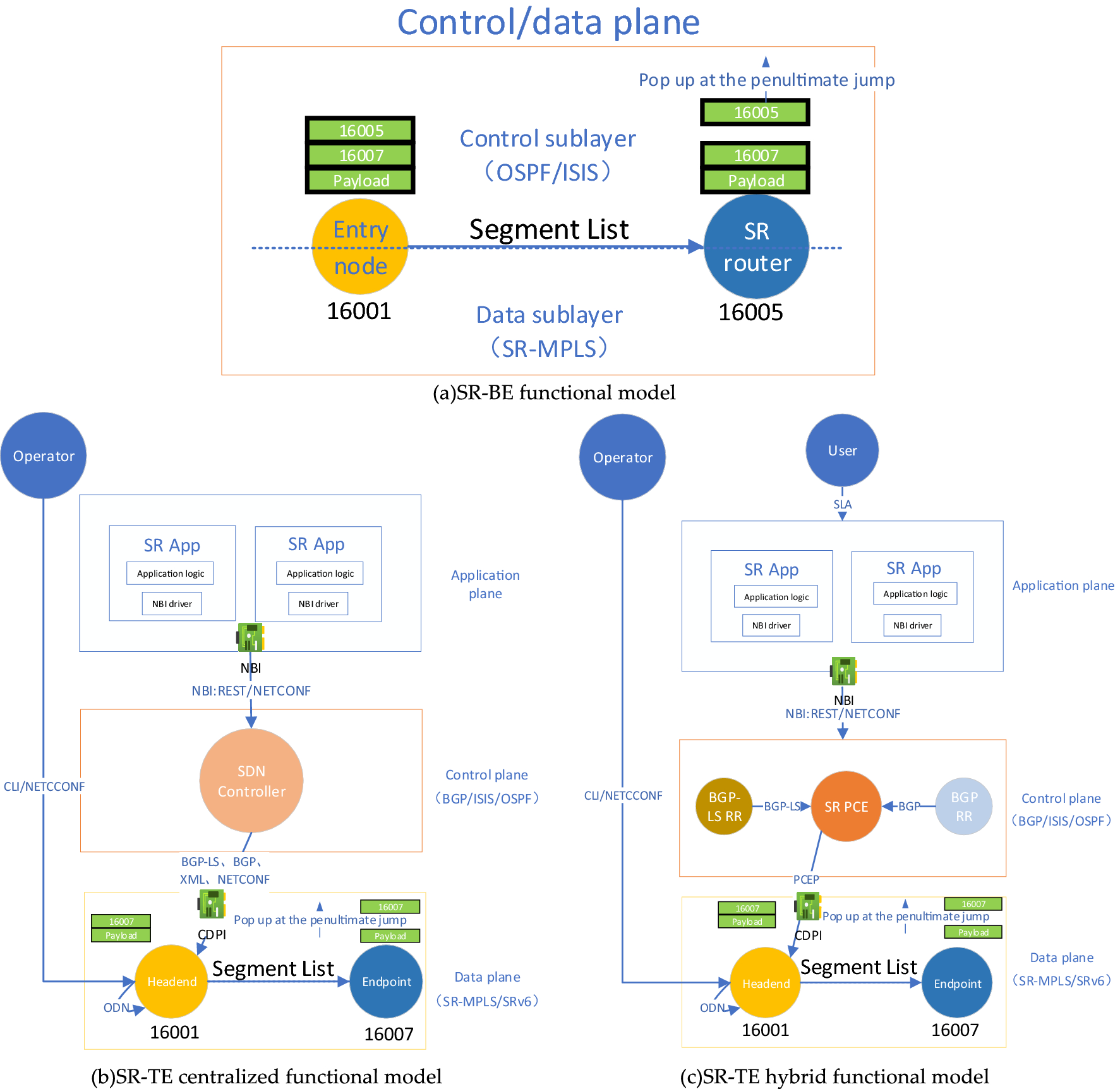
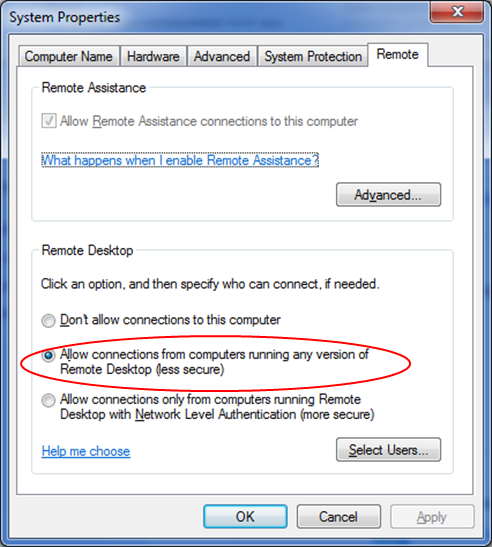
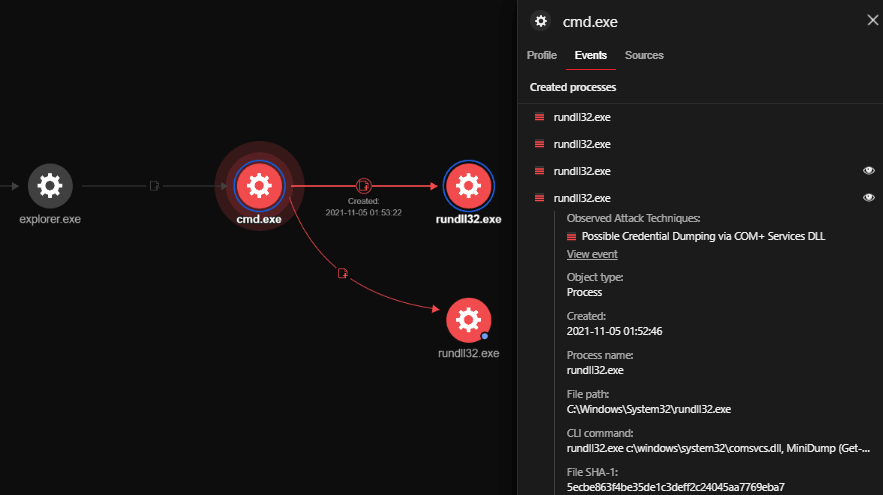
A data plane security model of segmented routing based on SDP trust enhancement architecture | Scientific Reports

Community-based rehabilitation intervention for people with schizophrenia in Ethiopia (RISE): results of a 12-month cluster-randomised controlled trial - The Lancet Global Health
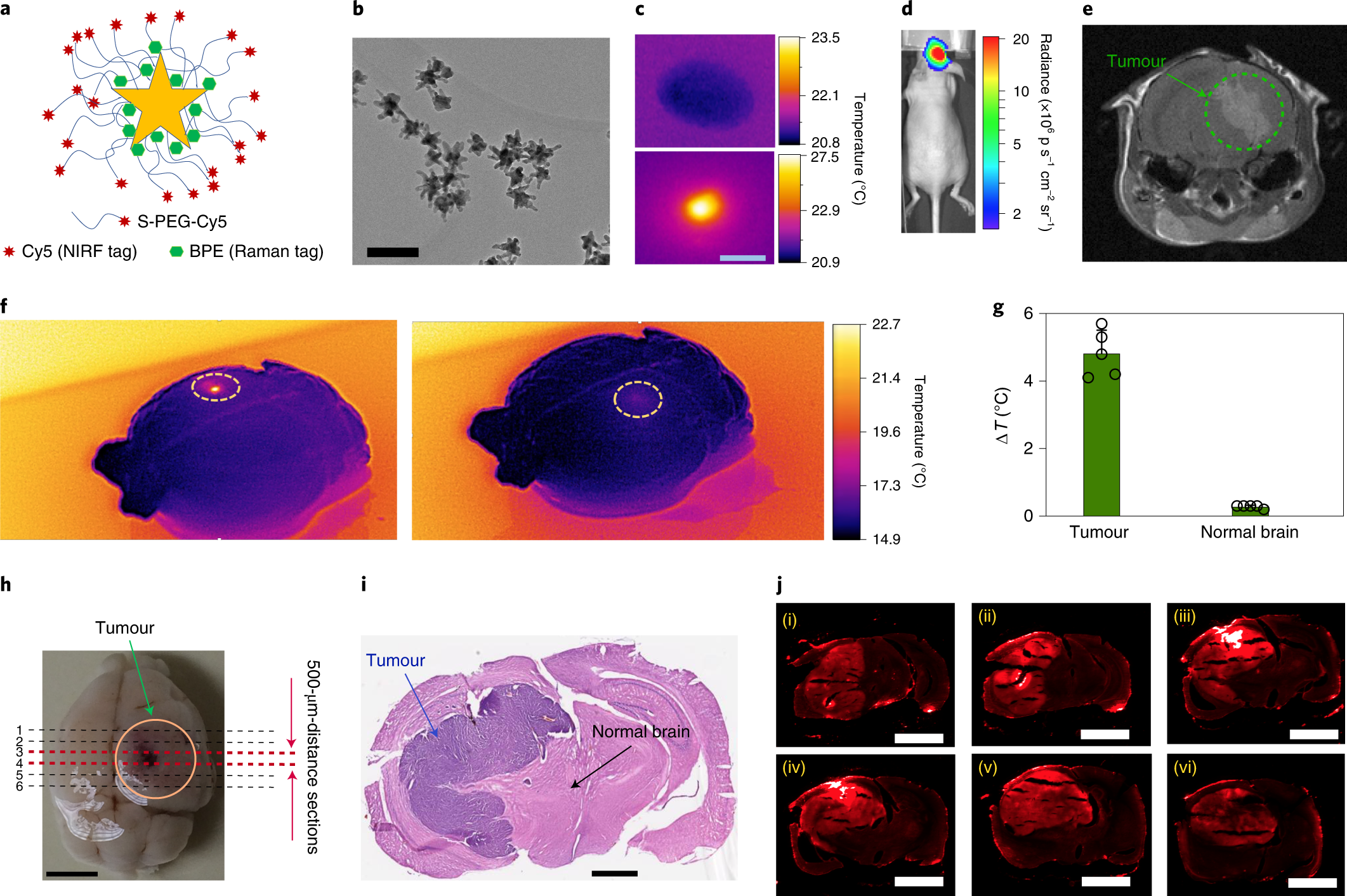



.png)